Security has always been an extremely important issue for Microsoft. Earlier this year, new security protocols were introduced to ensure the ongoing security of all parts of the cloud-based Microsoft Dynamics (which powers Bevica) and Office 365 ecosystem. In this blog, we take a look at these changes and how they impact on authentication protocols within the Microsoft stack. In particular, we take a look at Multi-factor Authentication.
What changes have been made to security protocols?
For many years, Microsoft applications, such as Business Central, used Basic Authentication to connect to servers, services, and API endpoints. Basic Authentication is a security protocol in which the application sends a username and password with every request, and those credentials are often stored or saved on the device. Traditionally, Basic Authentication was enabled by default on most servers or services, and was simple to set up.
However, as cybercriminals became more sophisticated, it was clear that Basic Authentication put companies at greater risk of data breaches and email disruption. Microsoft, therefore, announced in 2019 that Basic Authentication would be deprecated. Companies would no longer be able to use Basic Authentication for Outlook, EWS, RPS, POP, IMAP, and EAS protocols in Exchange Online. SMTP Auth would also be disabled if it was not being used.
Instead, Microsoft required organisations to move to Modern Authentication methods. The timetable for change started happening on 1 October 2022.
What is Modern Authentication?
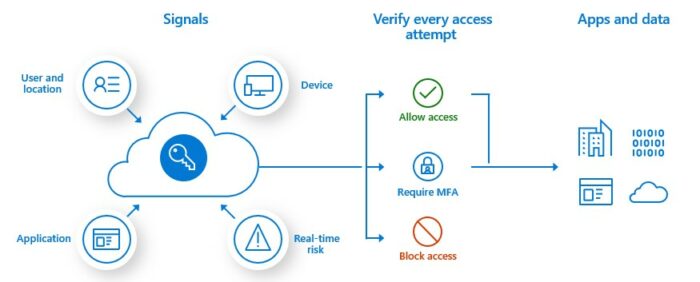
Modern authentication is an umbrella term for a combination of authentication and authorisation methods between a client (for example, your laptop or your phone) and a server, as well as some security measures that rely on access policies that you may already be familiar with. It includes:
- Authentication methods: Multi-factor authentication (MFA); smart card authentication; client certificate-based authentication
- Authorisation methods: Microsoft’s implementation of Open Authorisation (OAuth)
- Conditional access policies: Mobile Application Management (MAM) and Azure Active Directory (Azure AD) Conditional Access
The most popular form of Modern Authentication with many of our customers, with regard to Microsoft apps is Multi-factor authentication.
What is Multi-factor authentication (MFA)?
MFA is a security process where during the sign-in process users are prompted for an additional form of identification. This can be a code sent to their mobile phone or a biometric scan (such as a fingerprint or face scan).
How does Azure AD Multi-Factor Authentication work?
Azure AD Multi-Factor Authentication works by demanding two or more of the following authentication methods:
- Something you know, typically a password.
- Something you have, such as a trusted device that’s not easily duplicated, like a phone or hardware key.
- Something you are, biometrics like a fingerprint or face scan.
Azure AD Multi-Factor Authentication can also further secure password resets. When users register themselves for Azure AD Multi-Factor Authentication, they can also register for self-service password resets in one step. Administrators can choose forms of secondary authentication and configure challenges for MFA based on configuration decisions.
You don’t need to change apps and services to use Azure AD Multi-Factor Authentication. The verification prompts are part of the Azure AD sign in, which automatically requests and processes the MFA challenge when needed.
What additional forms of verification are available for MFA?
When users sign in to an application or service and receive an MFA prompt, they can choose from one of their registered forms of additional verification. Users can access My Profile to edit or add verification methods.
The following additional forms of verification can be used with Azure AD Multi-Factor Authentication:
- Microsoft Authenticator app
- Windows Hello for Business
- FIDO2 security key
- OATH hardware token (preview)
- OATH software token
- SMS
- Voice call
There are a number of factors to consider when selecting which form of verification to use. Click here for some advice from Microsoft on which passwordless option to choose.
How do I enable and use Azure AD Multi-factor Authentication?
You can use security defaults in Azure AD tenants to quickly enable Microsoft Authenticator for all users. You can enable Azure AD Multi-factor Authentication to prompt users and groups for additional verification during sign in.
For more granular controls, you can use Conditional Access policies to define events or applications that require MFA. These policies can allow regular sign in when the user is on the corporate network or a registered device, but prompt for additional verification factors when the user is remote or on a personal device.
How can TVision Technology help?
If you have any questions about the deprecation of Basic Authentication, the introduction of Multi-factor Authentication and how they affect your Business Central / NAV working environment, contact us and we’ll be happy to discuss it with you.

